At this point, rhetoric’s relationship to attention is perhaps self-evident. One of the more recent treatments of rhetoric and attention is Richard Lanham’s The Economics of Attention, which argues that rhetoric is a key tool for attracting and managing attention, our most scarce resource.[note]Lanham, The Economics of Attention, xi.[/note] This argument is part of a long history in rhetorical theory, one that has been concerned with how attention is allocated, marshaled, and controlled. Perhaps rhetoricians have been focused on attention because it is so clearly linked to the art of persuasion—one must manage the audience’s attention by way of claims, evidence, and tactics. Or maybe this attention to attention is due to accusations that rhetoric is itself a distraction. Still, we know that Lanham would not make the argument that rhetoric is on the side of attention and that its “other” is distraction, for this would result in what he’d call a “weak defense” of rhetoric—there is “good” rhetoric and “bad” rhetoric. Mine is good; yours is bad.[note]Lanham, The Electronic Word, 158.[/note] A “strong defense” would instead insist that rhetoric is as much about how distraction pulls apart (“a drawing or being drawn asunder”) as it is about how attention attaches to things.[note]“Distraction, N.”[/note]
Given this, what does the rhetorician have to say about distraction, a topic that has encouraged a cottage industry of books and thinkpieces? This was one question our working group brought to Matthew Crawford’s The World Beyond Your Head, and it was an apt one given that Crawford himself argues for an interdisciplinary and synthetic effort when tackling what he calls the “cultural problem” of attention.[note]The World Beyond Your Head, 5–7.[/note] Crawford’s book attempts “an ethics of attention for our time,” an ethics that is primarily concerned with ethos, with our contemporary environment. He positions the book as “a capacious reflection on the sort of ethos we want to inhabit.”[note]Ibid., 7.[/note] Crawford’s ideal ethos is concerned with “the right to not be addressed,” and one of his more provocative proposals is for an “attentional commons.”[note]Ibid., 13.[/note] He argues that we have ceased to see our own attention as something to be defended, and his primary concern is the “mechanized” demands made on our attention from afar: “The ever more complete penetration of public spaces by attention-getting technologies exploits the orienting response [of humans] in a way that preempts sociability, directing us away from one another and toward a manufactured reality, the content of which is determined from afar by private parties that have a material interest in doing so.”[note]Ibid., 10.[/note] He goes on: “The valuable thing that we take for granted is the condition of not being addressed. Just as clean air makes respiration possible, silence, in this broader sense, is what makes it possible to think.”[note]Ibid., 11, emphasis in original.[/note] Crawford’s attentional commons would preserve and protect the right to not be addressed so that we might have time and space to think.
When Crawford describes the noise that crowds us on a daily basis (advertisements at the airport, the buzzing of electronic devices, the crush of email), I identify. But this identification points directly at the larger cultural problem that rhetorical theory can and should help address. This narrative of distraction is an extremely privileged one. The first person plural of Crawford’s book (and of similar texts by Sherry Turkle, Nicholas Carr, and others) does not always acknowledge that “our” narrative of distraction is not a universal one.[note]Turkle, Alone Together; Carr, Nicholas, The Shallows.[/note] By this, I do not mean that “we” are not distracted. Indeed, everyone is distracted—some more than others. But the call for a less distracting ethos does not always recognize the imbalances in the system, the unequal distribution of distraction.
Distraction names the demands that we do not want to face. These are demands we have not chosen, and they arrive whether or not we have invited them. What do such demands announce? For one, it announces an answerability that was always there. This is the affectability or exposedness theorized by Diane Davis in Inessential Solidarity: “an affectability or persuadability that precedes and exceeds symbolic action.”[note]Davis, Inessential Solidarity, 19.[/note] Distractability is another word for persuadability—an unavoidable openness to the other.[note]Crawford likens distractability to obesity, since it feeds on “hyperpalatable” stimulation. The World Beyond Your Head, 16.[/note] However, something else is at work here as well. Distraction announces, even if only for a moment, that you are mismatched with the environment, that something about this space at this particular moment is out of whack for you. To distract is to pull apart, to pry you away from what you were trying to do. It is an uncoupling of you and your environment. You are trying to pay attention, and a distraction arrives. If distraction pulls apart, then attention seeks out connection—the Latin attendere means to turn or stretch towards something. If I am paying attention to something, I turn toward it and connect with it. Distraction disrupts the circuit. If our contemporary environment has encouraged ruminations on the dangers of distraction, it is an indication that those of us accustomed to seamless interactions (interactions with a world seemingly form-fitted to our body) are being pulled asunder.
Crawford proposes an attentional commons that values the “right to not be addressed.” It should be noted here that Crawford recognizes the impossibility of such a proposal. Others will arrive to address us. The ethos he describes is aspirational. However, to even aspire to such an ethos indicates a position of mastery. A cursory glance at our contemporary ethos makes it clear that the right to not be addressed is actually best understood as a privilege. There are numerous examples we might point to here.[note]This was the most distracting part of writing this essay. I wanted to point to so many examples: Anita Sarkeesian being “addressed” with threats of rape and murder for pointing out misogyny in videogames; Ta-Nehisi Coates’ story in Between the World and Me of his five year old son being shoved by a white woman in New York City; accusations that Black Lives Matter protestors at a Bernie Sanders rally were distracting from the fact that Sanders is a champion of civil rights. Each of these cases points to the question of distraction in a different way, and in a longer essay I would hope to tie them together.[/note] But here is one. In an essay called “Slow Poison,” Ezekiel Kweku recounts his thoughts while driving up the coast of California. Kweku was thinking about the deaths of Sandra Bland and Samuel DeBose, two unarmed African-Americans killed by police officers:
If stopped by the police, I thought to myself, I would set my phone to record audio and put it on the passenger seat. I would send a tweet that I was being stopped and had every intention of complying with the police officer. I would turn on Periscope and livestream the stop, crowdsourcing witnesses. I would text my family and tell them that I was not feeling angry or suicidal, that I was looking forward to seeing them soon. There would not be time to do all of these things, but maybe if I prepared in advance I could pull off one or two of them. What all of these plans had in common were that none of them were meant to secure my safety, but rather to ensure that my death looked suspicious enough to question. I was figuring out how to enter evidence into the inquiry of my own death.[note]Kweku, “Slow Poison.”[/note]
Minutes after considering these various strategies, Kweku was pulled over by police. When the flashing lights appeared, he did not carry out his plan: “Instead, I rifled through my last few minutes on the road, trying to work out what I’d done to draw the officer’s attention. I quickly ruled out everything I could think of.”[note]Ibid.,[/note] The police officer said he’d made an unsafe lane change but later admitted that it might have been another driver. Kweku was free to go. This episode could not be more different than Crawford’s discussions of distraction, and this is primarily because the world is much better suited for Crawford’s body than it is for Kweku’s. Think of the attention it requires to live in a world so ill-fitted for your body. Think of how distracting it must be. Think of Kweku’s right to not be addressed.
Crawford might respond that this is a different kind of demand on our attention, that he is concerned with mechanized and manufactured attempts to capture our attention from “afar.” His preferred ethos would insist that the distractions of virtual reality (representations) that pull us away from one another be set aside in favor of engagements with reality. That reality involves both face-to-face interactions and engagements in skilled craftsmanship. Crawford links our contemporary problem of distraction to the Enlightenment impulse (his primary villain is Kant) to see the world as a set of representations: “The creeping substitution of virtual reality for reality is a prominent feature of contemporary life, but it also has deep antecedents in Western thought. It is a cultural project that is unfolding along lines that Immanuel Kant sketched for us: trying to establish the autonomy of the will by filtering material reality through abstractions.”[note]Crawford, The World Beyond Your Head, 73.[/note] Kant’s disregard of the noumenon in the name of the phenomenon lands us in the realm of information overload. We are inundated with representations, leading us away from reality. Crawford’s solution to this problem is a focus on an engagement with reality by way of skilled practices that help structure our attention (practices such as glass blowing and organ making).
By engaging with the real (and here he primarily means wood, glass, and metal) we can re-center our attention and attempt to stave off distraction. For Crawford, such skilled practices are not about achieving autonomy—quite the opposite. They are about “submitting” to material constraints and about seeing oneself as part of a longer history and tradition of craft, traditions that offer methods of tuning out immaterial, virtual noise and focusing in on material reality: “External objects provide an attachment point for the mind; they pull us out of ourselves. It is in the encounter between the self and the brute alien otherness of the real that beautiful things become possible.”[note]Ibid., 27.[/note] This choice to submit to material reality is an attempt to attach to objects and to fend off being pulled asunder by the unwanted address.
This choice does not present itself to everyone. When Crawford describes “submitting” to material constraints in order to experience agency, or when he argues for the value of listening to teachers and elders (when learning the traditional techniques for playing the violin, blowing glass, or constructing organs), I’m thinking of Kweku’s encounter with the material constraints of law enforcement and of the cultural traditions he drew upon in that moment. This encounter is perhaps not the “skilled practice” that Crawford has in mind, but “The Talk” that African Americans have with their children about what to do when they are approached by police is a very different way of dealing with the uninvited address. The skilled practice of not being killed by police requires an attention to detail. Here’s Kweku again, after being pulled over:
I did not want to directly contradict him, which might anger and provoke him. But neither did I want to admit to an infraction which I did not commit. I did not want to know the consequences of that admission. It occurred to me how little was under my control.[note]Kweku, “Slow Poison.”[/note]
In an encounter with “brute alien otherness,” Kweku draws upon the lessons learned from “The Talk,” but the result was not so much beauty as survival. The differences between organ-making and “The Talk” are obvious. However, maybe the similarities are more compelling. They both structure attention through rituals that “relieve us of the burden of choice and reflection, as when we recite liturgy.”[note]Crawford, The World Beyond Your Head, 23.[/note] They both rely on a tradition passed down from experts to apprentices. They both involve a very direct engagement with material reality.
Maybe I’m being a killjoy. Maybe this whole conversation has been a red herring, pulling Crawford’s argument away from its proper focus on the distractions of a hypermediated world and the value of skilled practices. I don’t think my argument here is unrelated to Crawford’s, but even if what I have offered is a distraction, it would still serve my methodological ends. In “Feminist Killjoys (And Other Willful Subjects),” Sara Ahmed suggests that the feminist killjoy is part of the broader project of a queer phenomenology—a phenomenology that would aim to defamiliarize and estrange:
Phenomenology helps us explore how the familiar is that which is not revealed. A queer phenomenology shows how the familiar is not revealed to those who can inhabit it. For queers and other others the familiar is revealed to you, because you do not inhabit it. To be ‘estranged from’ can be what enables a ‘consciousness of.’ This is why being a killjoy can be a knowledge project, a world-making project.[note]Ahmed, “Feminist Killjoys (And Other Willful Subjects).”[/note]
The willfulness of a queer phenomenology results from a desire to reveal that which is concealed. In a different essay, Ahmed suggests that this revelation can be especially difficult “when a whole world is organised to promote your survival, from health to education, from the walls designed to keep your residence safe, from the paths that ease your travel, you do not have become so inventive to survive.”[note]Ahmed, Sara, “Selfcare as Warfare.”[/note]
A queer phenomenology would offer rhetoricians a way to turn their attention to distraction. It would, by definition, be distracted. Queer phenomenology is “a disorientation device; it would not overcome the disalignment of the horizontal and vertical axis, [instead] allowing the oblique to open another angle on the world.”[note]Ahmed, “Orientations,” 566.[/note] This is a method for seeing the red herring not as a distraction but as a reminder that the smoothness and continuity of a space is fictional—that my right to not be addressed is not a right but a privilege. The task of such a research program would be to focus not so much on the content of the distraction but on the affective experience of being distracted, which announces that the world you inhabit is not a matter-of-fact one—that this moment of distraction that you are experiencing is worthy of your attention. Perhaps rhetorical theory’s focus on attention has led to theorizing the experience of those for whom the world was built. This theoretical effort should be reoriented toward, in Ahmed’s words, “that which slips.” It should be more open to the embodied experiences of distraction and to the bodies that never quite easily slotted into place.
Demands on our attention are announcing something. But what? Who or what is addressing us, and who are “we”? From where does this address come? We don’t know, but an answer that involves sealing ourselves off from the address is one that is only available to a select slice of the population. Thus, it is not a solution at all. Perhaps “we” have not been distracted enough.
References
Ahmed, Sara. “Feminist Killjoys (And Other Willful Subjects).” Scholar & Feminist Online 8, no. 3 (2010). http://sfonline.barnard.edu/polyphonic/print_ahmed.htm.
———. “Orientations: Toward a Queer Phenomenology.” GLQ: A Journal of Lesbian and Gay Studies 12, no. 4 (2006): 543–74.
Ahmed, Sara. “Selfcare as Warfare.” Feministkilljoys. Accessed August 28, 2015. http://feministkilljoys.com/2014/08/25/selfcare-as-warfare/.
Carr, Nicholas. The Shallows: What the Internet Is Doing to Our Brains. New York: W. W. Norton & Company, 2011.
Crawford, Matthew B. The World Beyond Your Head: On Becoming an Individual in an Age of Distraction. New York: Farrar, Straus and Giroux, 2015.
Davis, Diane. Inessential Solidarity: Rhetoric and Foreigner Relations. 1st ed. University of Pittsburgh Press, 2010.
“Distraction, N.” OED Online. Oxford University Press. Accessed August 28, 2015. http://www.oed.com.proxy.libraries.rutgers.edu/view/Entry/55730.
Kweku, Ezekiel. “Slow Poison.” Pacific Standard. Accessed August 28, 2015. http://www.psmag.com/health-and-behavior/even-if-the-police-dont-kill-me-a-lifetime-of-preparing-for-them-to-just-might.
Lanham, Richard A. The Economics of Attention: Style and Substance in the Age of Information. Chicago: University of Chicago Press, 2006.
Lanham, Richard A. The Electronic Word: Democracy, Technology, and the Arts. University Of Chicago Press, 1995.
Turkle, Sherry. Alone Together: Why We Expect More from Technology and Less from Each Other. First Trade Paper Edition edition. Basic Books, 2012.
Ultra Business Tycoon III claims to be a port of “an old edutainment game from the 90’s,” but anyone familiar with it’s designer, Porpentine, knows that this is a feint. Designer of games like Cyberqueen (a sci-fi romp in which the player is tortured and dismembered by a computer) and Happiness Simulator (which starkly demonstrates the difficulties of being transgender), Porpentine has little interest in the typical Tycoon game. Unlike Game Dev Tycoon or Prison Architect, it should be clear early on that this game is not really interested in presenting the player with god-like powers. Porpentine’s game does everything it can to undercut the empowerment that defines the tycoon genre. Rather than managing from above and learning the processes and procedures of corporate systems, the player of Porpentine’s game is caught in a messy world of sweating and bleeding bodies. (In fact, Porpentine’s favorite subject is body fluids, making her work a perfect fit for our discussions around the theme of “fluid” at SLSA.) The game offers a framing narrative about domestic abuse, which is revealed to the player in a disorienting way. What begins as a business simulator transforms into something else. The player slowly learns that he or she is not controlling a character who is “a prominent businessreplicant in the money business” but is instead controlling a character who is controlling that character.
The game’s attempt to frustrate and disorient has meant that players offer mixed reviews. Some see it as a brilliant critique of the Tycoon genre, and others think that the game is too opaque to offer the kind of experience they’re seeking. Of course, frustrating game experiences are nothing new. Maybe frustration is the result of poor design, or maybe it’s an attempt by so-called art games to use frustration as a rhetorical tactic, or maybe it just reflects a game’s utter indifference to us. But Ultra Business Tycoon III is important for another reason—it offers an example of something I’d like to call “obfuscated mapping,” a strategy for understanding life in late capitalism. Or, better, a strategy for demonstrating the utter impossibility of understanding that life. If Frederic Jameson’s cognitive mapping sought a way to understand how subjects struggle to position themselves in increasingly disorienting postmodern spaces, then Porpentine’s approach to what Jameson calls “hyperspace” acknowledges the unknowability of systems (computational or otherwise) and attempts to engage that uncertainty on its own terms.
In Programmed Visions, Wendy Chun argues that the graphic user interface is a cognitive map, a direct response to the postmodern condition (a response that, she argues, might work too well by providing the user too great a sense of control). We can see videogames as the apotheosis of this form. The vast majority of games teach us that what we do makes sense, that we can control an environment, and that there is a clear relationship between actions and results. But interfaces can be designed with other goals in mind. In the remainder of my time, I’d like to consider not only Porpentine’s game but also the platform on which it was created (Twine) in terms of obfuscated mapping—attempts to map our relationship to global capital that begin from the premise that the territory is infinitely complex and perhaps even impossible to map.
Ultra Business Tycoon III
Porpentine’s game mimics the “edutainment” games of a previous era, down to the .nfo file that comes with the game.
The game begins as what seems to be an absurd take on the Tycoon genre, and the player controls a character who is tasked with, among other things, taking down corporate competitors, gaining more money, and killing anyone who gets in the way. Right from the start, we see that this Tycoon game is not exactly what we might be expecting. For instance, while we can enter a skyscraper (right in line with genre expectations), we can also choose to enter Subterranean Trash Zone II or Oasis Zone VI (where “the leylines of capitalism are strong”). Upon entering the Trash Zone, we are met with, among other things, a putrid smell and a Bee Gate. The game only gets more bizarre from here, but Porpentine’s point is that this absurd world is perhaps not much more absurd than those of games like Railroad Tycoon or Lemonade Tycoon. All of these previous examples of the genre afford the player a great deal of power as they attempt to become millionaires and rule the world. The main difference, of course, is that Porpentine’s primary interest is in holding a mirror up to the capitalistic impulse.
But the game’s biggest innovation (and its relevance to a discussion of obfuscated mapping) is not this direct critique of capitalism. Its most interesting feature is the moment at which we discover that this game, made in the Twine platform, has us playing the role of a player of Ultra Business Tycoon III. We get different clues about this, from humorous commentaries about the length of cut scenes to clickable text that reads “press spacebar” (pressing one’s spacebar does nothing—we must click the text).
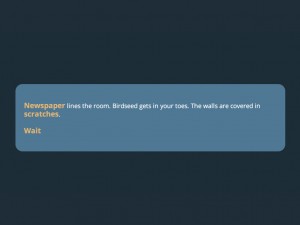
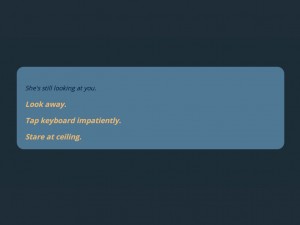
But the most jarring moments happen when we learn that our player character lives in a dark world shaped by domestic violence. When the player character’s sister interrupts a session of Ultra Business Tycoon III, there is a tortured exchange that makes it clear that the player character does not know how to talk to the sister nor how to deal with the abuse both of them face on a regular basis.
Porpentine has created a helpless character in a no-win situation. Faced with a sister who is likely running away to avoid abuse, we can “stare at the ceiling” or tap our keyboard. But there is no option for “save sister” and definitely not one for “talk to your sister about the problem.” In these moments, we are playing two games at once—a game called Ultra Business Tycoon III and another, nameless and much more devastating game that is far more distrubing than a world of Bee Gates and weaponized potassium.
Obfuscated Mapping
The player of Ultra Business Tycoon III lacks much agency (and by “player” I mean both the person playing the Twine game and the in-game character playing Ultra Business Tycoon III). There are often no clear links between player actions and results, something that runs counter not only to popular videogames but also to the GUI designs with which most of us are used to working. Wendy Chun has argued that such GUIs should be seen as examples of Jameson’s cognitive maps, designed to respond to the postmodern condition.
Stepping through how Douglas Engelbart’s NLS and Vannevar Bush’s Memex have informed contemporary interfaces, Chun demonstrates how the GUI puts “us” in the driver’s seat. This becomes especially clear in Engelbart’s “mother of all demos”: “Through our identification with Engelbart via his demo we emerge as sovereign subjects—subjects of files. Not accidentally, Engelbart’s tasks are administrative: compiling lists, assigning ownership to files” (85). As Engelbart copy/pastes and clicks with his mouse, he is in control, and his face melts with the screen to demonstrate how he is the one navigating this space. Command and control is coded right into the design of the original GUI, and this megalomaniacal user reaches new heights in a number of contemporary videogames, as players expect to be in a position of control.
Of course, Chun also argues that this is a fiction, that computers are demonic, always “inhabited by invisible, orphaned processes” that run in the background, often completely out of the user’s control. In a response to this lack of control, Chun argues, we actively work to forget that our interfaces are maps. Instead of seeing them as representations, “we try to inhabit them, and, by inhabiting them, we turn them into something other than a map” (93).
Instead of seeing maps as imperfect attempts, we are encouraged to see them as successes that “clear up confusion and establish the user as the sovereign subject, in control of what she sees: she controls technology that transparently reveals her relationship to the invisible laws of computation” (89). Chun’s argument is not that we need fewer interfaces or that we should abandon these attempts to map. Instead, she is suggesting that we fully embrace the idea that computers are “metaphors for metaphor” and that we engage in the practice of mapping by recognizing “the artificiality of metaphor…mak[ing] strange and estranging the world around us” (94). By embracing this approach, we could begin to see all maps as “deliberately odd and artificial” (94).
The notion of obfuscated mapping that I’m describing in by way of Ultra Business Tycoon III is my attempt to embrace the computer as a metaphor for metaphors. I am, of course, pulling the term “obfuscation” from the idea of obfuscated coding, a practice of writing unnecessarily complex computer programs. In an essay entitled “A Box, Darkly,” Nick Montfort and Michael Mateas argue that obfuscated code can both shed light on programming languages (pointing out quirks and affordances of certain languages) and can productively defamiliarize our encounters with code (10). For Montfort and Mateas, obfuscated code demonstrates that a program could be written another way, even if that other way is tortured and unduly complex. Such code reminds us that utility is but one outcome of computer programming.
But questioning utility does not have to mean alienation, and obfuscated code is strangely hospitable to those willing to take it up. Montfort and Mateas argue that obfuscated code and weird languages “invite theorists and critics of new media to look into the dark box of the machine and see how creativity is at work in there, too” (10).
While Montfort and Mateas are primarily concerned with expanding the aesthetics of code, my aim is to understand the work of Porpentine and others as obfuscated maps—as attempts to map life in late capitalism. If obfuscated code exposes the workings of a programming language and calls for reconsiderations of how code is written, it does so by way of a particularly frustrating path. Yes, obfuscated code invites interaction, but it simultaneously frustrates that interaction by making itself opaque and difficult. Like Porpentine’s Ultra Business Tycoon III (and a host of other games made in the Twine platform), obfuscated code eschews clarity in the name of complexity. In Porpentine’s version of the Tycoon game, it’s not immediately clear who or what I am controlling, let alone what I’m trying to accomplish or how I might “win” the game. Such complexity offers a much more fitting account of life in global networks of capital, which never make it clear how one can or should act and which often make it difficult to directly link action with result.
Twine: A tool for Obfuscation?
As we consider obfuscated mapping as a tactic for life in late capitalism, it’s worth considering not only Porpentine’s game but also her tool of choice, Twine. Interestingly enough, the design view of Twine, the platform used to create Ultra Business Tycoon III, presents the designer with a map of passages and links, one that puts the designer in the “command and control” seat. From this perspective, it seems odd to argue that Twine offers any kind of obfuscation. Still, even if we were to argue that Twine developers are caught up in the GUI control fantasy, this wouldn’t prevent us from considering Twine games as sufficiently obfuscated.
In a platform study entitled “Untangling Twine,” Jane Friedhoff argues that Twine’s development as a platform must be considered alongside the community that helped make that platform successful—namely, LGBTQ writers and designers. A free, open-source platform, Twine has offered the non-programmer a tool for creating and publishing text-based games. Friedhoff argues that the features of the system (it’s free, easy to use, and offers a simple distribution model) can be linked directly to the types of games we find developed in Twine. The taboo material dealt with in many Twine games would likely not be available on game consoles or Steam (though, Twine games have found their way to these spaces in certain instances). Indeed, it’s difficult to imagine a game like Ultra Business Tycoon III emerging on any other platform, but other games like Encyclopedia Fuckme bring this argument into sharper focus.
With Twine, we see how a platform and a user community are often woven together. There is a convergence between the technical affordances of a platform that relies on links and clicks and the concerns of the LGBTQ community. Twine’s focus on forcing choice (see, for instance, the scene referenced above when the player of Ultra Business Tycoon III does not really engage her sister) simulates the gender choices foisted upon those in the LGBTQ community, and the inability to escape those decisions tie that community to this platform in interesting ways. In addition, many Twine games play up a lack of player agency. A review of Twine on Rhizome puts it this way: “Twine text-based games emulate our limited agency within our daily experiences with work, lovers, friends, art, life, and as such have proven a valuable cultural form for people who, in their daily lives, must work within a limited set of choices.” The review goes on to argue that many Twine games attempt to “highlight the arbitrariness of the user’s decisions, their lack of agency.” This is especially clear in one of Porpentine’s other games, Howling Dogs, which Leigh Alexander describes this way: “Howling Dogs is an abstract, often surreal experience centralized on the concept of confinement; even though it’s a text game, it feels spatial and non-linear, as the player must repeat certain conventions of self-maintenance.”
While Twine is anything but obfuscated as a design platform, it has created a way for LGBTQ designers to create disorienting experiences that leave the player with a confusing map and, often, a diminished sense of player agency. And there seems to be quite the need for such game experiences. Consider one player’s response to Ultra Business Tycoon III:
As a game, I found the biggest flaw to be how difficult it was to know what to do when (or even if there was a “right” or “best” or even “productive” thing to do). As a story, I found it surprisingly compelling, in the same way that a kid feels about poking a dead thing with a stick. But the appeal wears off pretty quickly.
A response like this one reveals a player is so trained to see player characters as heroic that he misses the central premise of the game: That the pure, frictionless control of many games is a fiction and that the character in Porpentine’s game, hiding in a bedroom playing Ultra Business Tycoon III, feels so trapped in a spiral of domestic abuse, depression, and isolation that she can’t actually step outside of the “passive” responses that so frustrate this player. It would seem obvious that the limited options provided (similar to those offered in another popular Twine game called Depression Quest) are meant to evoke passivity. There is no saving the princess in Ultra Business Tycoon III. What’s the most ethical response here? To stare at the ceiling? But this player and many others have been trained by a range of interfaces to see this as a bug rather than a feature.
If, as Chun argues, the GUI was designed as a response to late capitalism and if that response has essentially worked too well by offering up an illusion of control, then games like Ultra Business Tycoon III might offer one possible way forward for those attempting to understand the disconnect between bodies and space in networks of global capital. Perhaps obfuscated mapping is best understood by turning not only to Twine and Twine games but to the array of practices and strategies deployed by LGBTQ writers. These writers have used Twine to describe lives in which concepts like agency and control are especially fraught, lives that offer a particularly extreme version of the vertigo and displacement many associate with late capitalism. This community (along with its tools and theories) seems the best place to turn for ideas about how to build obfuscated experiences, maps that can serve to remind us that all of our attempts to understand contemporary space are failed ones and that this can be a starting point rather than a dead end.
]]>It sure would be great if “literature” and “rhetoric and composition” weren’t viewed as completely separate spheres of activity. Once a month or so, I make the argument that literary studies and rhet/comp could do a much better job of actually talking to one another (this works in both directions). But that argument is very difficult to make when our professional organizations and departmental infrastructures insist on (benefit from?) antagonistic relationships.
All I know is that I have great interactions with my colleagues in literary studies. That is, at the level of individuals, it is possible to speak across this divide. So, when the MLA takes all the various flavors of rhetoric/writing/composition/literacy studies and lumps them into a single category (while drawing careful distinctions between other areas within the various subdomains of literary studies), I can only say this: Collaborate and talk to *individuals* (in your own department and elsewhere) and ignore the confusing actions of dinosaur organizations that are 30 years behind the times. You’ll find that those individual interactions are more fruitful than any attempt to get the dinosaur to budge.
]]>On Friday, I posted the first chapter of a new project called Making Machines, a book/website that will combine (or “mashup”) works from the rhetorical tradition to build new theories and concepts. This first chapter combined George Campbell’s The Philosophy of Rhetoric and Cicero’s De Oratore in a mashup entitled “Sonic Eloquence.” Here’s a brief excerpt from the “mashup” essay:
“Together, Campbell and Cicero offer us a theory of sonic eloquence, a term that would help us consider eloquence not only in terms of words and meaning but also in the tones and musicality of the voice. These two texts offer detailed accounts of how the human voice persuades and even how it does so in a way that sneaks underneath our cognitive radars. Thus, sonic eloquence operates at various registers, at both conscious and unconscious levels. Their focus is on the human voice, but we could extend Cicero and Campbell’s discussions to other realms of sound. Sonic eloquence need not be confined to the conscious choice of the orator or even to human voices. Various frequencies might be persuasive, suggesting that sound itself can be eloquent or ineloquent, persuasive or unpersuasive. Thus, sound is not only a tool we use but is also a force that operates on us.”
That essay and its accompanying digital material – a brief discussion of how looping audio reveals sonic eloquence and a tool called Sound Arguments that examines audio in various ways – were generated over the course of a month. As I mentioned in a blog post on July 8, the rules were that I had to finish this chapter before the Making Machines bot spit out another pairing of texts. The new pairing appeared this past Saturday, and my next task is to combine Stanley Fish with Giambattista Vico. (The fact that the bot has generated two pairings of white guys says something about what we call “the rhetorical tradition,” and I’ve been wondering if it might be worth writing an algorithm that weighted the works rhetorical tradition differently. That weighting could account not only for race and gender of authors but also for geography or historical moment. If the rhetorical tradition skews west, white, and ancient, would it make sense to balance things out algorithmically?)
Generating this material over the course of a single month was an interesting experience, and (perhaps unsurprisingly) the self-imposed deadline was generative. I found myself “watching the clock,” making sure I’d budgeted enough time to read, write, design, collaborate, and code things. The arbitrary one-month deadline also meant that Eddie Lee and I had to release an alpha version of the Sound Arguments tool that we’ve been hatching. Even given it’s rough state, I’m particularly proud of this part of the project because it demonstrates the kinds of collaborations that can emerge in these “mashups.” In future chapters, I’m hoping to be able to team up with programmers and designers that can help me make various machines. Given that future chapters will be created during the course of three months instead of one month, I should have a bit more time to enlist the help of others.
Sound Arguments is still under construction, but I’m extremely happy with what Eddie and I were able to accomplish in just a couple of weeks. The Making Machines site explains the tool and offers some examples of what it can do for those interested in analyzing (or even composing with) audio.
There was one example that I wasn’t able to include on the site prior to the deadline, so I thought I’d share it here. As the site explains, Sound Arguments allows us to represent sound in multiple ways. It generates visual representations (spectrograms) and audio representations (a series of tones or “notes” for a given audio clip). I’m especially interested in the tones generated, but maybe that’s because I’m still learning to read spectrograms. The site contains some examples of these outputs, but here’s another example: Barack Obama’s 2004 DNC address.
Here’s the opening of Obama’s speech:
Download Clip
Here are the tones generated by Sound Arguments:
Download Clip
Here are those two audio files overlaid:
Download Clip
Now, we can go back and isolate the phrase “crossroads of a nation”:
Download Clip
And we can loop it:
Download Clip
And we can grab the Sound Arguments tones associated with that phrase:
Download Clip
If you go back to the initial clip above, it’s nearly impossible not to hear “crossroads of a nation” as a song. As the Radiolab episode I cite in the “Sonic Eloquence” chapter makes clear, this is largely because looping audio draws our attention to the music that lives in language. While it’s weird to think that Obama is “singing” here, it’s also difficult to ignore the song that’s playing right there in the middle of his sentence. Is this a rhetorical tactic? Or is it merely something that lives inside of speech, playing upon our reason and emotion in unpredictable ways? What are the rules of sonic eloquence, and how would we follow and/or teach them? These are some of the questions opened up by the first chapter of Making Machines.
This discussion of “opening up” questions is important, because I want to highlight that this is about as far as the “Sonic Eloquence” chapter goes. In the course of a month, I was (I hope) able to ask some interesting questions about sound an eloquence, questions that were actually exposed by the discussions of sound in Cicero and Campbell. Making Machines is about making theory and making digital objects, but it’s primarily about launching new directions for rhetorical research and rhetorical practice. So, I hope the chapter makes its own “sound argument” and that it finds plenty of textual evidence for tracking sonic eloquence through these two texts, but what happens with the concept “sonic eloquence” or the Sound Arguments tool is an open question that I hope others in the field will see fit to help me pursue.
]]>
On Wednesday, July 10, 2013 a robot will be giving me a writing assignment. That robot is a Twitterbot called @makingmachines, and it will pull two random texts from the table of contents of Patricia Bizzell and Bruce Herzberg’s The Rhetorical Tradition.
So, my “assignment” will be generated by an algorithm, but the writing itself will also follow a set of procedures. That is, it will be constrained in various ways. I’ll say more about those constraints below, but first I should take a moment to answer the question many are probably asking right now: “Why?”
Let me begin by explaining the roots of this project. A few years ago, I began thinking about using the “mashup” as a method for generating theoretical concepts. I described this method in a previous blog post and also in a Computers and Composition article. Without getting into too much detail about these previous writings, my aims were to think of the musical mashups of DJs like Girl Talk as a method for rhetorical invention. I asked students to mashup rhetorical theorists, and I even carried out some of these mashups myself. I began to consider using this method as part of an extended argument about digital rhetoric, and I started thinking about how I might randomly combine rhetorical theorists to generate new concepts for digital rhetoric. These concepts would be attempts to build theories and concepts for creating and analyzing texts and objects in digital spaces.
In the last few years, my interest in this project has expanded. I am now interested both in the mashup method and in a detailed consideration of the procedures that might generate those mashups. Part of these expanded interests are linked to my attempts to consider how nonhumans participate in rhetorical ecologies. In addition, I have been inspired by the work of Darius Kazemi, Mark Sample, and others who have explored how computation can be used to generate things (from shopping lists to jokes to rap lyrics).
From this group of interests and influences comes a project I’m calling Making Machines, which takes up the making of machines (digital, discursive, or otherwise) and how we might consider theories to be “making machines” – machines that help us make things. Given that I’m a rhetorician, Making Machines is focused on understanding and expanding “the available means of persuasion.” My hope is that the concepts that emerge out of this project will be useful for those trying to persuade and to those trying to understand how persuasion operates. My primary focus is on digital rhetoric – on how persuasion operates in digital environments, but my hope is that this discussion can extend into other types of environments as well.
With this background in mind, here are two reasons for pursuing this project. As I write and make, more reasons will emerge, but this is what is currently motivating the project:
1) This project aims to make explicit the algorithms and procedures that already shape writing, argument, and theoretical innovation. I see rhetorical theory as a set of algorithms for generating and interpreting arguments. Rhetorical theory offers us a set of procedures by which we might make arguments or understand the arguments of others. Making Machines is an attempt to take that premise one step further, to view rhetorical theories as machines and to make some of my own machines.
2) Making Machines attempts to demonstrate what emerges from human-machine collaborations. We make machines, and they make us. For me, one of the clearest articulations of this comes in Katherine Hayles’ Electronic Literature: New Horizons for the Literary. Hayles urges us to consider “the human and the digital computer as partners,” and she describes how “humans engineer computers and computers reengineer humans in systems bound together by recursive feedback and feedforward loops” (47-8). This new project puts me into these recursive loops, alongside various machines, and asks what emerges from such collaborations. In order to ask this question, humans have to be willing to see that they are sometimes “machinic.” This is what I’m trying to do by placing myself at the mercy of various machines, rules, and procedures.
I’m writing about this project in the interest of sharing both my process (the procedures that shape the project) and the eventual products (the theoretical “mashups” that will emerge from this process), but I’m also writing this so that I am accountable to a broader audience. (For instance, sharing this process means that I can’t just run the @makingmachines bot until I get a favorable pairing.)
So, here are the constraints that shape the writing and making of Making Machines:
1) I am tasked with “mashing up” the two texts named by @makingmachines in order to create a new rhetorical concept. I can only use these two texts. If the bot selects a text that is excerpted in The Rhetorical Tradition, I will be using the entire text and not just the exerpt.
2) This “mashup” will be an essay, and that essay must be exactly 3000 words.
3) I must then use the concept that I’ve created to generate some kind of digital object.
4) I must complete composition of both the essay and the digital object before the bot generates the next pairing (the bot currently generates a new pairing every month). [Note: This time period will likely have to change once the academic year starts. For this “pilot” run, I’m giving myself a month.]
5) I will publish the results at http://makingmachines.jamesjbrownjr.net. [Note: This page does not yet exist.]
I’ll post more about this project as it progresses. You can also follow @makingmachines if you’re interested in seeing the pairing it generates on Wednesday.
]]>I wrote a coda for the talk that won’t be quite as rhetorically effective a few months from now. It took up some questions about polling and algorithms that emerged in the wake of President Obama’s victory, and I had hoped to link my discussion of robot writers to these questions as a way to link my talk to recent events. But the kairotic window is quickly closing on that discussion, so I thought I’d post the coda here. I’ll find some new material for the coda in the spring. It shouldn’t be difficult, given that we are inundated with algorithms, narratives, and databases.
The bulk of my talk deals with the algorithmic journalists developed by Narrative Science, a company that transforms data into narratives by way of software. Many see the emergence of robot writers as a threat to the supposedly “human” realm of writing and narrative. That threat is often quickly dismissed, since robots can’t do what “we” do. However, I see these algorithmic journalists as exposing more than just another iteration of the “robots vs. humans” battle. After all, any piece of writing is the result of an algorithm that transforms data into narrative.
The scope of the data, the complexity of the algorithm, and the angle of the story may all change based on who or what is writing. But we are not all that different from robots. And if we imagine all writing as algorithmic, then we can begin to think of algorithmic thinking as a way to toggle between the worldviews of narrative and database. Lev Manovich famously developed this theoretical pair in The Language of New Media to describe how new media stages a kind of battle between narrative and database. The narrative worldview posits a single path through data, making sense of data by way of selection and exclusion. The worldview of database is more inclusive (though it makes some determinations as well) and allows for more pathways through the data to exist simultaneously.
Algorithmic thinking provides a way to sit in the liminal space between narrative and database, and rhetoric presents a long tradition of algorithms that help us sit in that space. With rhetoric, we can toggle between these two approaches to the world. So, this is the talk in a nutshell. Obviously, I’ve moved quickly through this argument, and I’ve skipped some of the hard work of showing how rhetoric is algorithmic. But I’ll save that for my visit to Milwaukee in the spring. Instead, I want to jump to the coda mentioned previously. While I spend much of the talk on the robots of Narrative Science, the coda took up a different robot:

This robot has served, simultaneously, as hero and villain in recent weeks. Nate Silver, baseball stats geek turned political forecasting geek, has been the target of derision (and celebration, depending on your political leanings) during election season. Silver’s fivethirtyeight.com (and if you’re like me, you have burned Silver’s site into your laptop screen during the past months) examines the vast database of available polling data and combines it with numerous variables (the biases of certain polls, jobs numbers, historical voter turnout numbers) to project election winners. Like Narrative Science’s “meta-writers” (who write algorithms that generate stories), Silver and his team author algorithms which process data and generate narratives. He tells us stories about all of this data, helping us make sense of it. But if the hospitable network enables this kind of analysis, opening up databases to anyone willing to author algorithms that make sense of it, that same hospitality has been extended to those who believe that Nate Silver might be a witch. In the lead up to the election, Silver defended himself against those who for various reasons—partisan leanings and television ratings chief among them—insisted that the 2012 presidential election was a “tossup.” He even bet MSNBC’s Joe Scarborough, who refused to believe Silver’s projections of a relatively easy Obama victory, $1,000 that his projection of an Obama victory was accurate. Scarborough was just one of many pundits who pitted their “gut instincts” against Silver’s sophisticated statistical models. This was essentially a replay, on a different stage, of the battle between stats geeks and old, crusty baseball scouts. Numbers vs. “the eye test.” As we know, Silver came out on top as his model correctly predicted the electoral vote count.
Two weeks ago, Silver told Charlie Rose that he believes he knows why he is the target of people like Scarborough: “I think I get a lot of grief because I frustrate narratives that are told by pundits and journalists that don’t have a lot of grounding in objective reality.” This is how many of us have understood this controversy in the wake of Tuesday night’s result: Nate Silver uses data. Joe Scarborough uses narrative. The former always trumps the latter. But this draws too clean a line between database and narrative, splitting the two along a human/nonhuman axis. Thus, Silver might be a “witch” because he uses data, and Scarborough was safe (or safer) from being put on trial because he relies on his human instincts. But both Silver and Scarborough author algorithms that transform data into narrative. Silver’s narratives may have been proven more accurate and may have been grounded in “big data,” but we closely watched election returns on election night because the news media had convinced us that the election was close—a toss-up.
The algorithms of Scarborough, Hannity, and a host of pundits across the political spectrum generated narratives that persuaded many of us to hesitate before proclaiming the election to be “in the bag.” This is not to say that all algorithms are created equal or that the narratives spun by various political noise machines should be treated the same as those generated by logical claims and sound evidence. In fact, this is precisely the problem. We are struggling with ways to sift and sort these narratives, which are sometimes spun from the exact same data.
And there are narratives that are more accurate than others. Silver, after all, was right. But we should also recognize that Silver’s success was not an indication that “big data” will always triumph or that narrative is flawed and “all to human.” That success was the result of a sound algorithm, an authored artifact that stood as an argument for the best way to move between database of polling data and narratives about the winner of the election.
The very fact that no explanation of data can claim to be the explanation means that citizens and media consumers are in a difficult position. How are these various, competing, conflicting narratives to be judged and compared? Which narrative should be trusted? What choices is an algorithm making when generating a narrative? How might we reverse engineer that narrative and speculate about the what motivates it? How does one oscillate between the competing spheres of narrative and database?
Rhetoricians have spent millennia building a vast library of algorithms that can help us understand the motives at work as data is used to spin narratives. These procedures have not necessarily been put forth as algorithms, but reframing rhetoric as a body of theory that generates reading and writing machines presents us with a particularly useful approach to our contemporary predicament. If our present environment is hospitable to conflicting narratives, then we require ways of sifting through those narratives. Databases grow, meaning that narratives proliferate. Determining how one might judge those narratives is an urgent problem for those hoping to make informed decisions about information. Rhetorical theory, which has always been algorithmic, provides one way of dealing with this struggle.
]]>An edited version of my RSA 2012 presentation, “Paul Cret and the Decorum of Objects,” is now available at Ozone: A Journal of Object Oriented Studies:
]]>
I had to duck out of the Rhetoric Society of America Conference early, so I wasn’t able to stick around for the Graduate Student Reception. The reception featured presentations from junior scholars that addressed issues of publication and professionalization. I was invited to be a part of this panel, and I ended up creating a video to be played in my absence. That video is below, and here is a link to the Prezi that’s featured in that video.
This was an interesting presentation to put together. I ended up learning quite a bit about my own writing processes and collaborative efforts, and I was shocked to learn how long it actually took to get “Composition in the Dromosphere” published. I knew it took a while, but I had never counted the years, months, and days.
]]>Here’s a video of my presentation from this year’s Computer’s and Writing Conference. It was part of a panel that Jentery Sayers and Virginia Kuhn organized entitled “Hacking the Classroom.” I wasn’t able to attend in person, but Jentery was kind enough to let me send along this video in my place. A transcript of the talk is below. (Note: The student work I discuss is available at my course website.)
Transcript:
Something is in the air, and it seems that 2012 is the year of code. From Code Academy’s “Code Year” project to Cathy Davidson’s call for a fourth R (algoRithms) to New York Times articles about programming “for the rest of us,” there is a public conversation happening about how code is more than just a technical practice. My own attempts to hack the classroom during this past academic year have happened with these broader public discussions in mind. I recently joined a brand new program in Digital Studies at the University of Wisconsin-Madison. This interdisciplinary program offers an undergraduate certificate in Digital Studies and currently includes faculty from Art, Communication Arts, English, and Journalism. Our focus is on providing students with a broad range of digital skills, from the visual to the aural to the computational.
Given this global context (“the year of code”) and my local context (UW-Madison’s Digital Studies program), I’ve attempted to make this “the year of computational thinking” for students in my classes. And I guess you could say I’ve done this by hacking the classroom. For me, hacking is about exploring possibilities without worrying too much about what the end result will look like. I certainly hoped that students would leave the classroom with a better sense of that “4th R,” but I also knew that I was experimenting with technologies and assignments that were brand new to me.
During these classes, my own hacks of the classroom have been two-fold:
Hack #1: Studio Pedagogy
Influenced by my colleague Jon McKenzie, I have begun to see my classroom as a studio space. I have given students more time and space to make things. This has been helped along by my teaching schedule—the classes I taught this year met once per week, and this made it easy for me to compartmentalize time. For instance, we might spend 45 minutes discussing our reading and then the remaining hour and a half would be devoted to designing video games or interactive fiction. For me, this approach also emerged out of conversations with colleagues about teaching courses online. I tried to imagine what I’d say if an administrator who asked me why I needed classroom space. Why couldn’t I just teach my courses online? We need good answers to this question. Online courses can be a good solution to certain problems, but it is not a magic bullet. But we need strong answers to questions about online teaching and the value of synchronous classes. This is one good reason to hack the classroom and explore its various affordances. How would you respond to a department chair or administrator who asks you to offer your courses online?
Hack #2: Writing code in the writing classroom
In both classes, students wrote a significant amount of code. They used two different systems: Inform7 and Scratch. Both of these systems are designed for the novice programmer. Inform7 allows students to code using English language sentences, and Scratch offers a visual interface. I’d like to briefly describe two of the more interesting student projects:
Bully Be Gone
Bully Be Gone is a work of interactive fiction that intervenes in contemporary discussions about bullying. Rather than presenting statistics or anecdotes about bullying, this game places the player in a world and asks them to move through it. The game (spoiler alert) slowly reveals to the player that s/he is the bully. Actions that initially seemed like day-to-day activities of day (taking an apple or) are eventually revealed to be the actions of a bully, and the player must right each of these wrongs in order to finish the game.
Walker, Wisconsin Ranger
Walker, Wisconsin Ranger is an attempt to address Ian Bogost’s argument in Persuasive Games that political video games have largely failed to take advantage of the procedural affordances of games. Students were tasked with creating a game that addressed an issue in Wisconsin politics, and that game needed to make a procedural argument. Walker, Wisconsin Ranger, puts the player in the shoes of Governor Walker. Game play involves making budget cuts that inevitably affect approval ratings. The game makes a fairly complex procedural argument about politics and policy by immersing us in the world of Scott Walker.
In addition to these courses, I’m looking forward to teaching “Composition and Computation” in the fall. This is part of a Freshman Interest Group I designed. A cohort of twenty first-year students will be taking three courses together: first-year writing, a course called “Principles of Computation,” and my course, which will involve writing code and tinkering with Arduino boards.
I have very much enjoyed this year of computational thinking. And while the Digital Studies program has allowed me to hack the classroom and push the boundaries of composition and rhetoric, I have been excited to watch my students hack in the classroom.
]]>During the past year and a half, Dale Smith and I have been working on a project entitled “Rhetorical Distributions: The Event and the Archive.” This project began as an essay that attempted to link Alexander Galloway’s work on protocol and networks to conversations about public culture, rhetoric, and the circulation of discourse. We’ve also extended this research into discussions of code, digital poetry, and constrained writing. We have presented portions of this work at the 2011 Texas Institute for Literary and Textual Studies Symposium and the 2011 Computers and Writing Conference.
The essay version of this research has already been cited by one print publication, Byron Hawk’s essay “Curating Ecologies, Circulating Musics: From the Public Sphere to Sphere Publics” (which appears in the edited collection Ecology, Writing Theory, and New Media: Writing Ecology). Additionally, we have received at least five other requests for manuscript versions of this essay. People who attended the aforementioned conferences or who have found reference to the project on the conference websites want to read it and/or cite it. The problem is that Dale and I have had difficulty finding a publication venue for this essay. We’ve submitted it to various journals, each time getting different advice. Each set of reviewers recommended citing different scholarship, making different changes to the argument, and changing the focus of the essay. Part of the problem is that we are hoping to address various audiences in the essay, which is sometimes a difficult thing to do in scholarly journals.
This is the nature of scholarly publishing, and we’re not complaining. We will grant that there are flaws with the essay. However, we have decided to publish it online.
We’ve decided to do this for two reasons: 1) It is already being distributed through various scholarly networks (an interesting thing to consider, given the essay’s discussion of circulation and distribution); 2) We’re open to hearing more feedback about the argument. In fact, perhaps we’ll revise the piece and publish another version.
So, to this end, we’re releasing the essay in two different ways:
1) As a WordPress installation that uses Commentpress
Commentpress is a WordPress plugin developed by the Institute for the Future of the Book that allows readers to post comments on the entire piece and on each individual paragraph. We welcome feedback on the essay.
2) As a PDF. The version we’re posting was last revised in November 2011.
We’re hoping that this experiment yields feedback and continues the life of this project. We look forward to hearing from scholars in various fields as we think through the argument.
]]>